I have listed the links to my VCF Home lab build out below to make it easer for folks to find.


I have listed the links to my VCF Home lab build out below to make it easer for folks to find.

Blog Date: December 2025
In my previous post, I walked through the process of getting the VMUG Advantage token configured in the Cloud Foundation Installer, to establish the connection to the online depot and download the VCF bits, HERE. This post assumes those bits have all been downloaded successfully.
Before continuing with your VCF 9 home lab deployment, or even a production deployment, be sure to check out this post HERE, where I cover the updated password requirements for VCF, and how missing those requirements will cause the deployment to fail.
For a VCF 9 home lab running on hardware that’s not part of the VMware HCL, it will be necessary to bypass the vSAN ESA precheck during VMware Cloud Foundation (VCF) deployment using the Cloud Foundation Installer. If compatible vSAN ESA hardware is not available in your home lab, the deployment fails during the HCL validation phase. To bypass this, log in to the VCF Installer and append the following configuration parameter to the following /etc/vmware/vcf/domainmanager/application-prod.properties file:
echo "vsan.esa.sddc.managed.disk.claim=true" >> /etc/vmware/vcf/domainmanager/application-prod.propertiesNext, you’ll either need to restart the the appliance, or you can just restart the service with the following:
systemctl restart domainmanager 
I’ve been deploying VCF for customers since the 2.X days, so I have mixed feelings about this new wizard. However, I must say I do enjoy not having to fill in multiple deployment workbooks. I am deploying a greenfield VCF home lab, so I do not have existing components
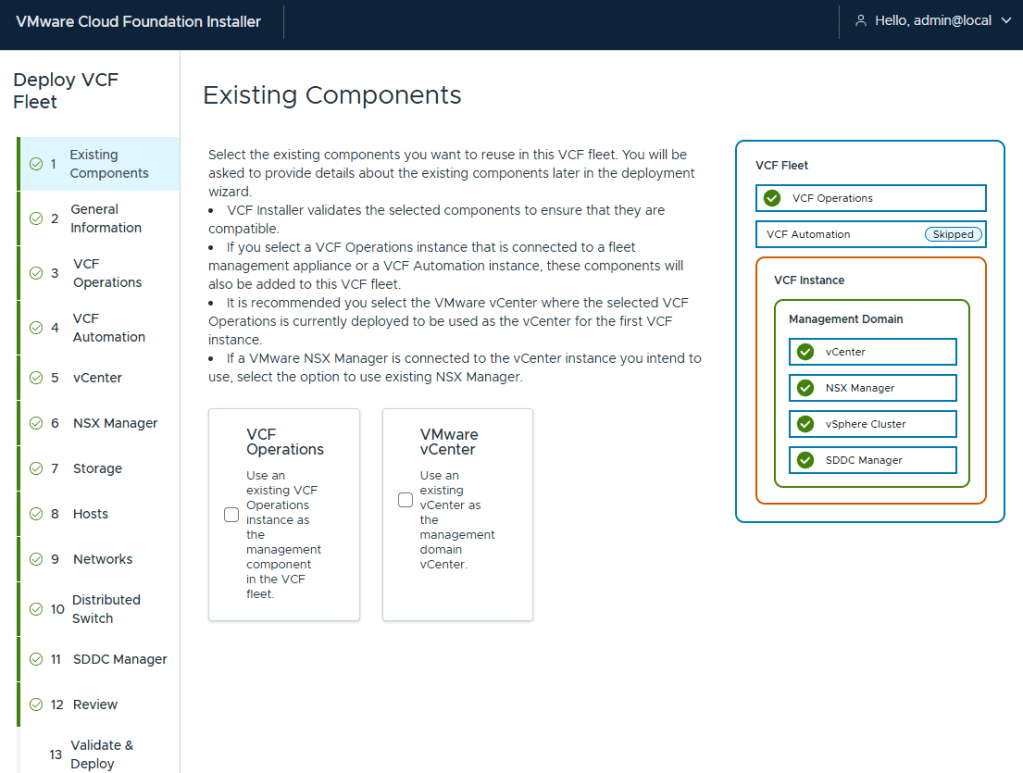
I elected to do a simple deployment for my homelab. I did notice through testing that the Installer will hallucinate if one of the NTP servers is not reachable. Later on during the pre-check validations, I saw error messages stating the NTP value was null. Probably my favorite was when it hallucinated NTP values that I did not configure, but said that it couldn’t reach them (duh). My only indication of the actual problem was that the pre-check failed when it couldn’t validate the ESX hosts connection to the second NTP and DNS server. I wonder how much vibe coding the VCF devs were doing that day?
I hadn’t deployed my second domain controller yet that I would also use as my second NTP source, and was hoping that I could set it during the Core VCF deployment, and deploy the server after. I ended up just deleting the second DNS and NTP server address in the Installer. I’ll just add it later. I left them configured on the ESX hosts.
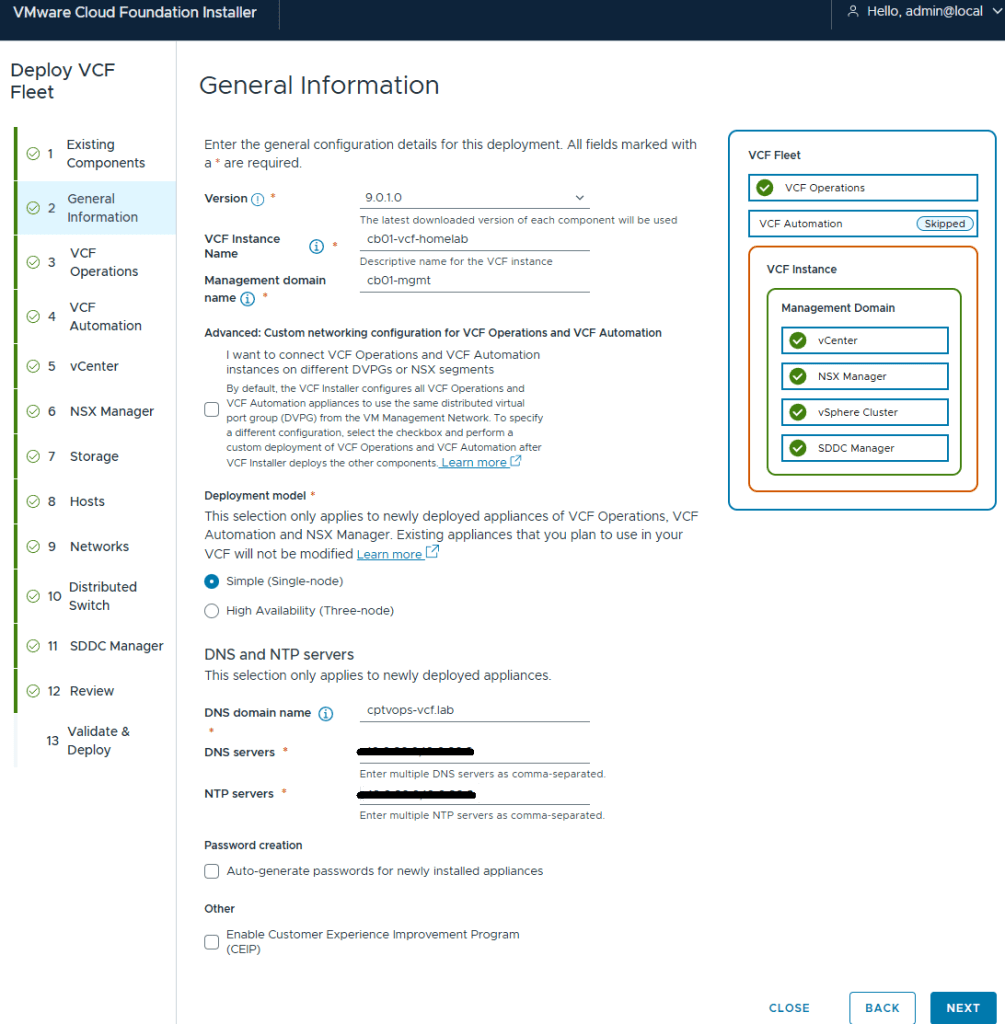
Deployment for VCF (Aria) Operations and Fleet Management Appliance (Aria Suite LCM)
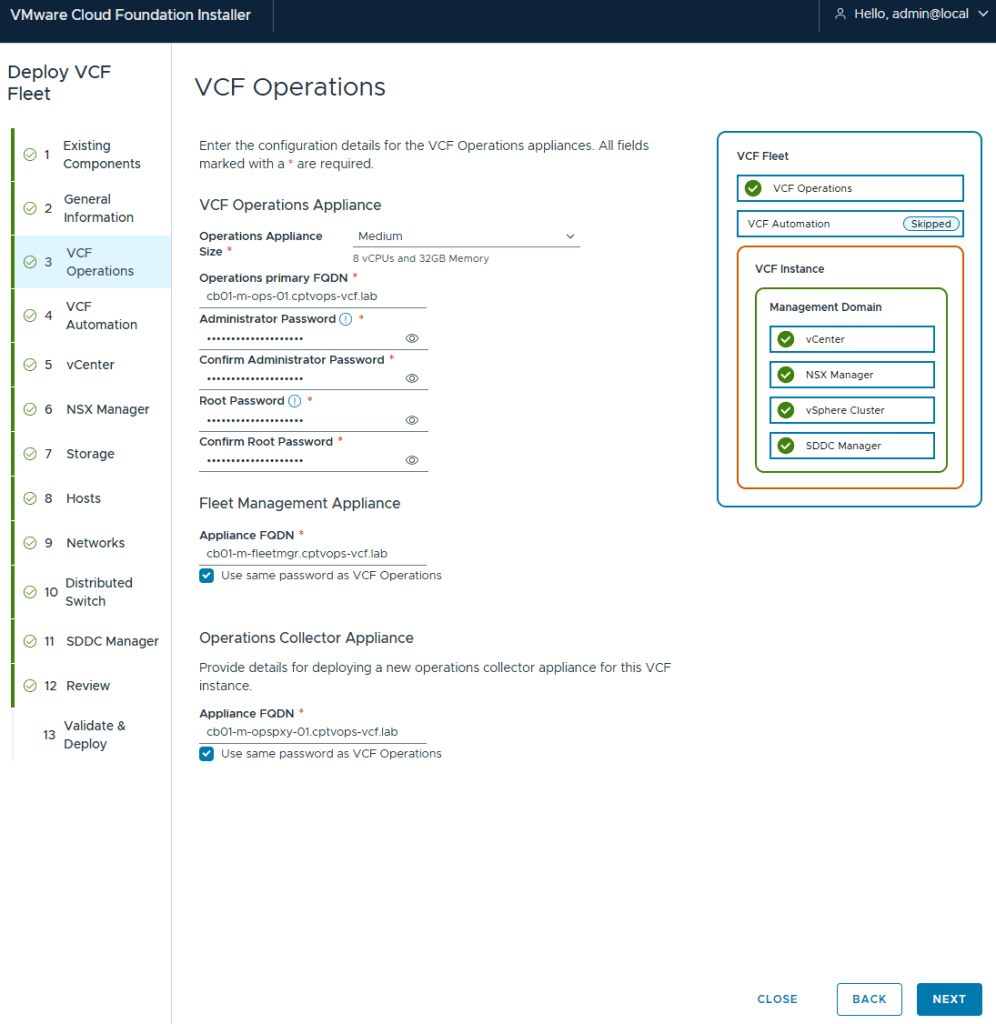
I elected to not deploy VCF (Aria) Automation. I’ll deploy this after.
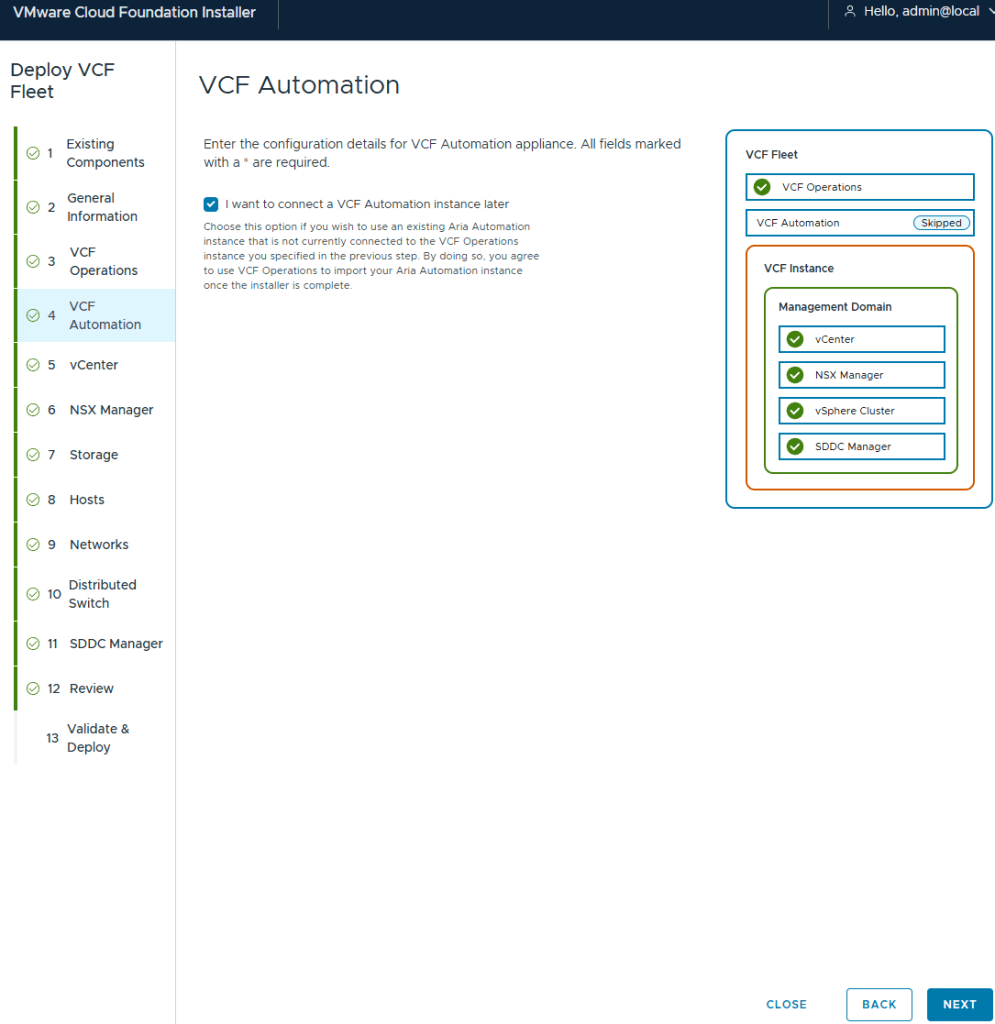
I deployed my management vCenter using the medium size to avoid the smaller appliances performance issues.
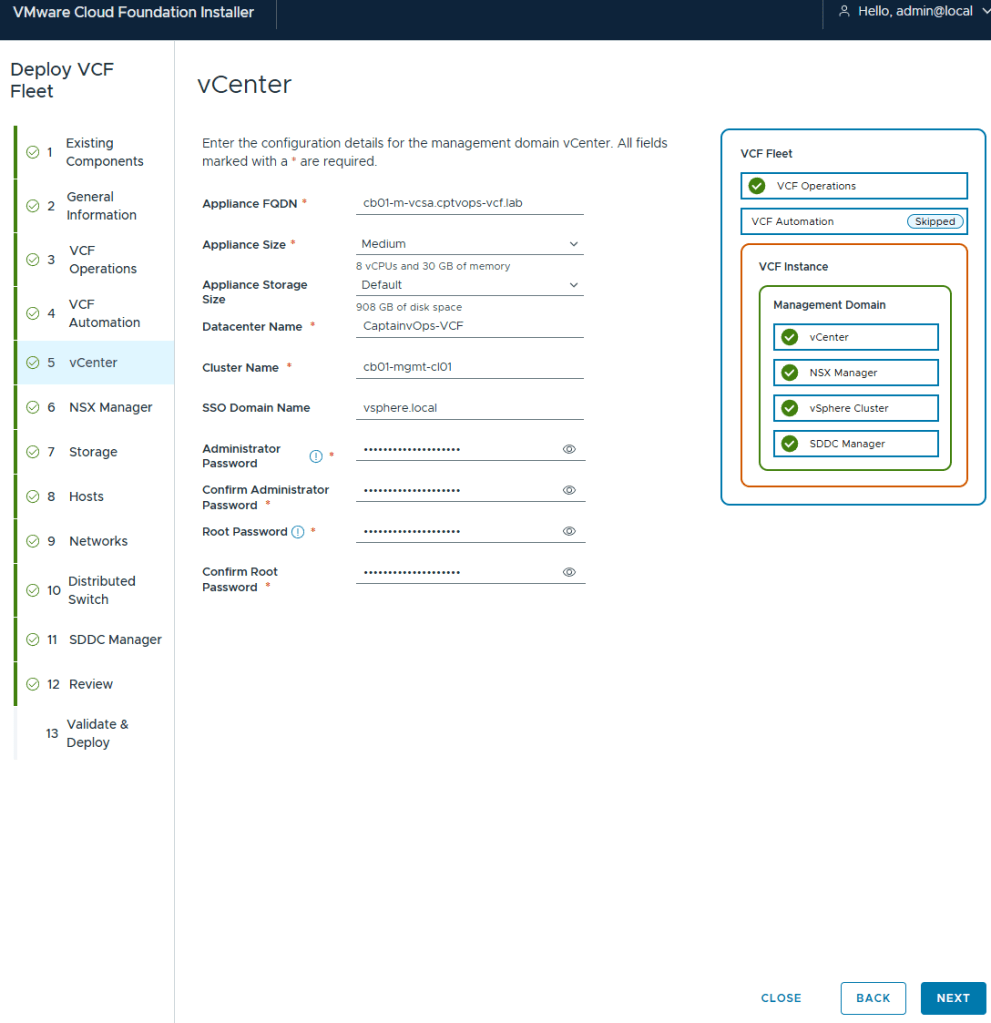
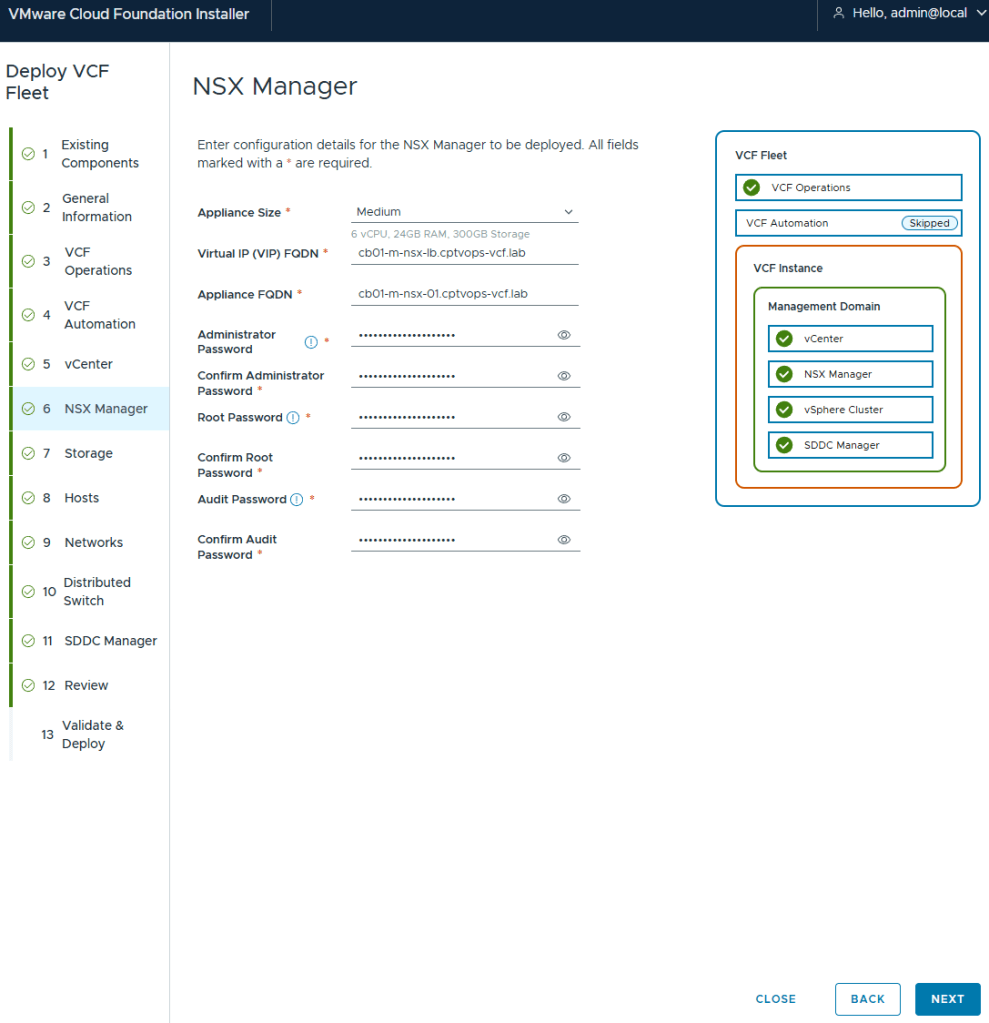
Even though the “simple deployment” was chosen, you are still required to define a Virtual IP for NSX.
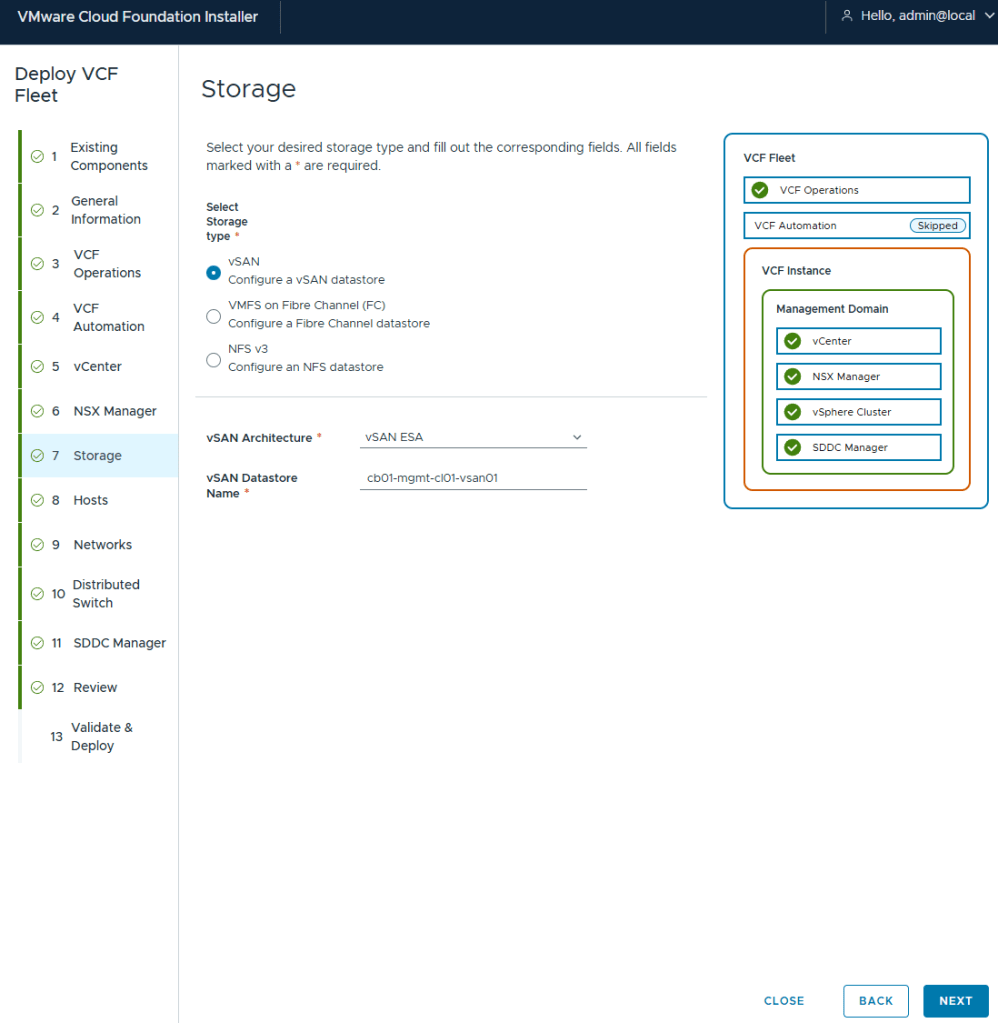
Out of all the VMware home labs I have built, this is my first using vSAN, but I wanted to try out ESA. In the past I avoided vSAN just because in certain situations it made host maintenance painful.
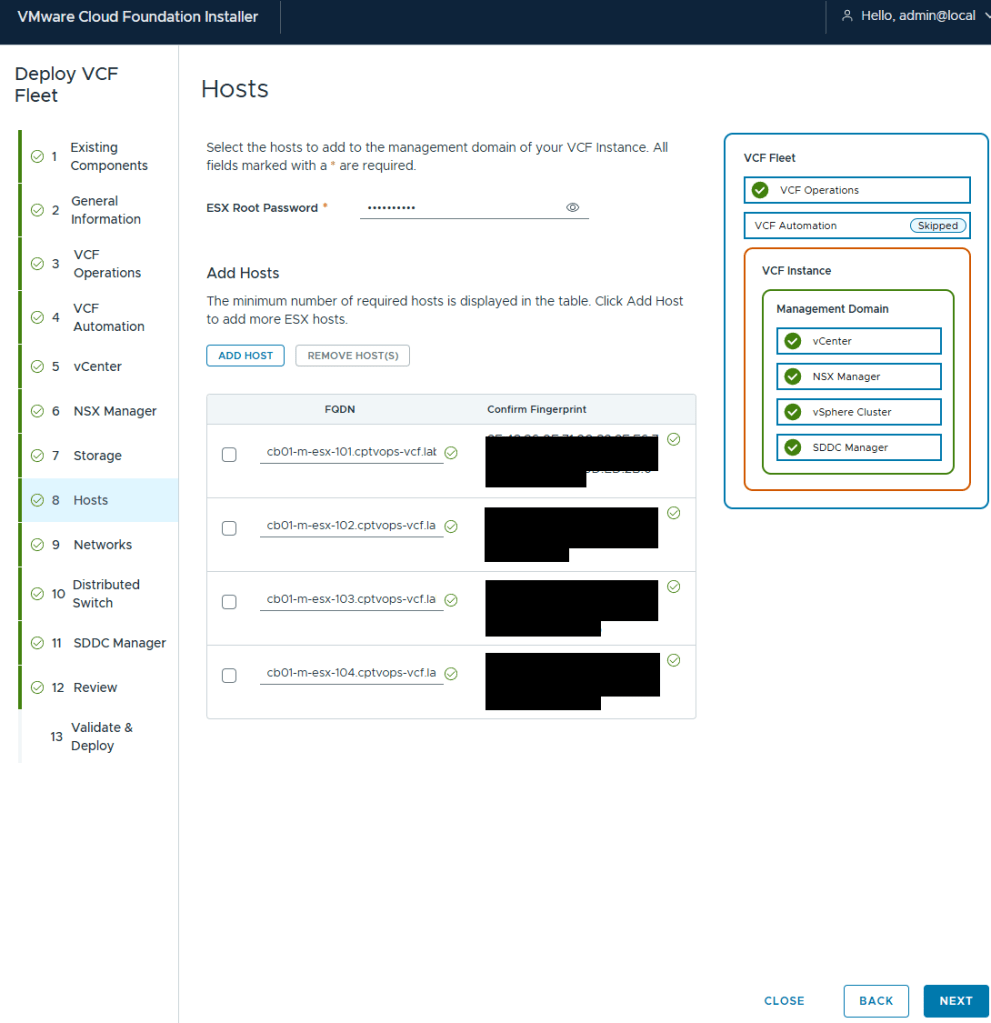
I’ve got my 4 MINISFORUM MS-A2 hosts added.
I elected to keep my deployment simple in my home lab, and have my management VMs share the same network as my ESX hosts.
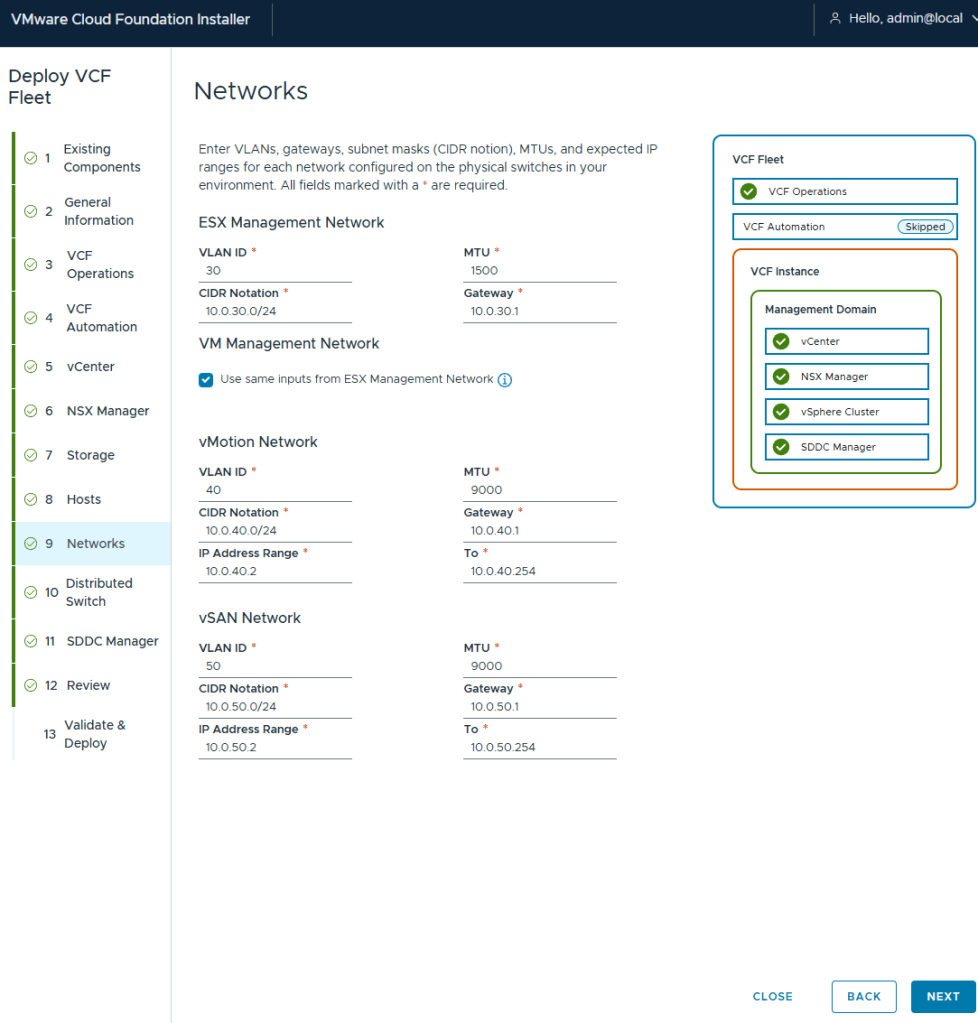
I chose the Default virtual distributed switch config
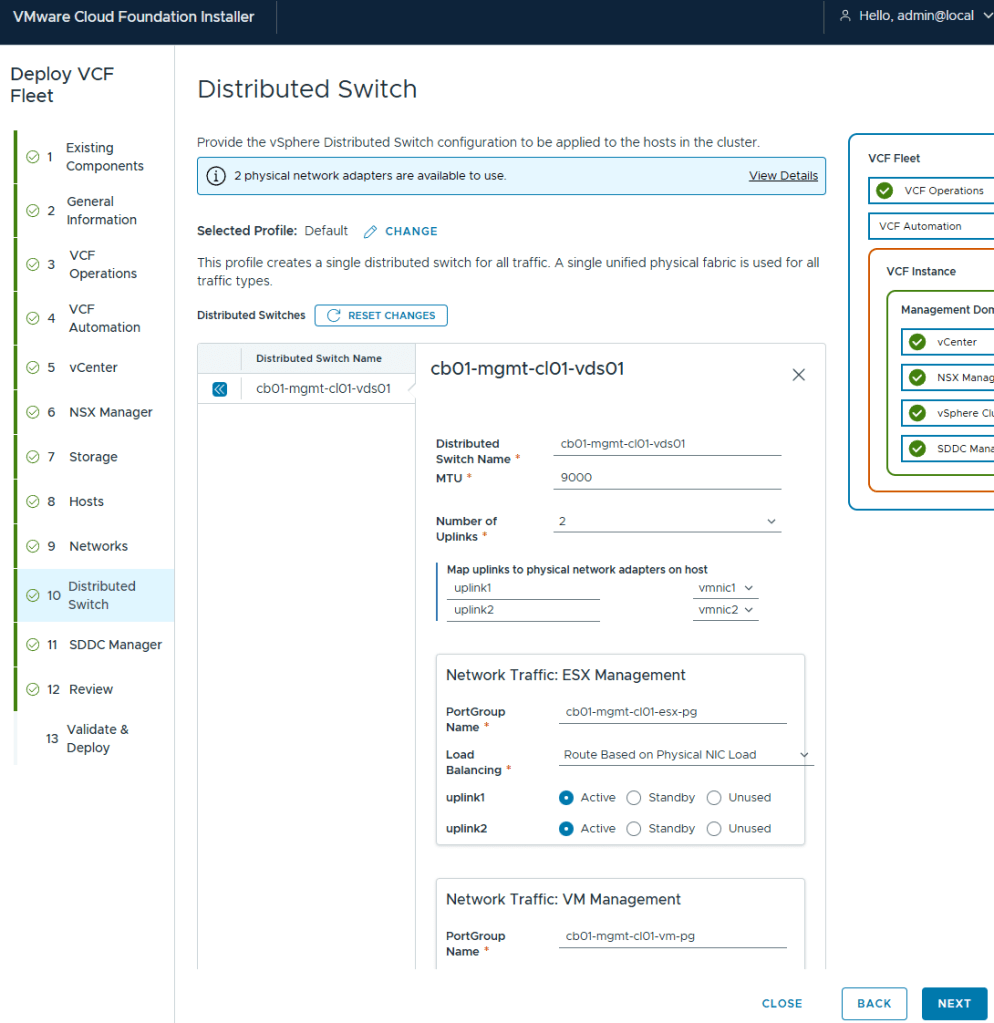
If you remember my previous post HERE, I talked about what will happen on this screen if you did not use a 15 character password for the local user (admin/Administrator).
As expected, the pre-check validation returned a WARNING on the vSAN ESX Disks Eligibility for not being on the HCL. This needs to be Acknowledged before the [DEPLOY] button becomes available.
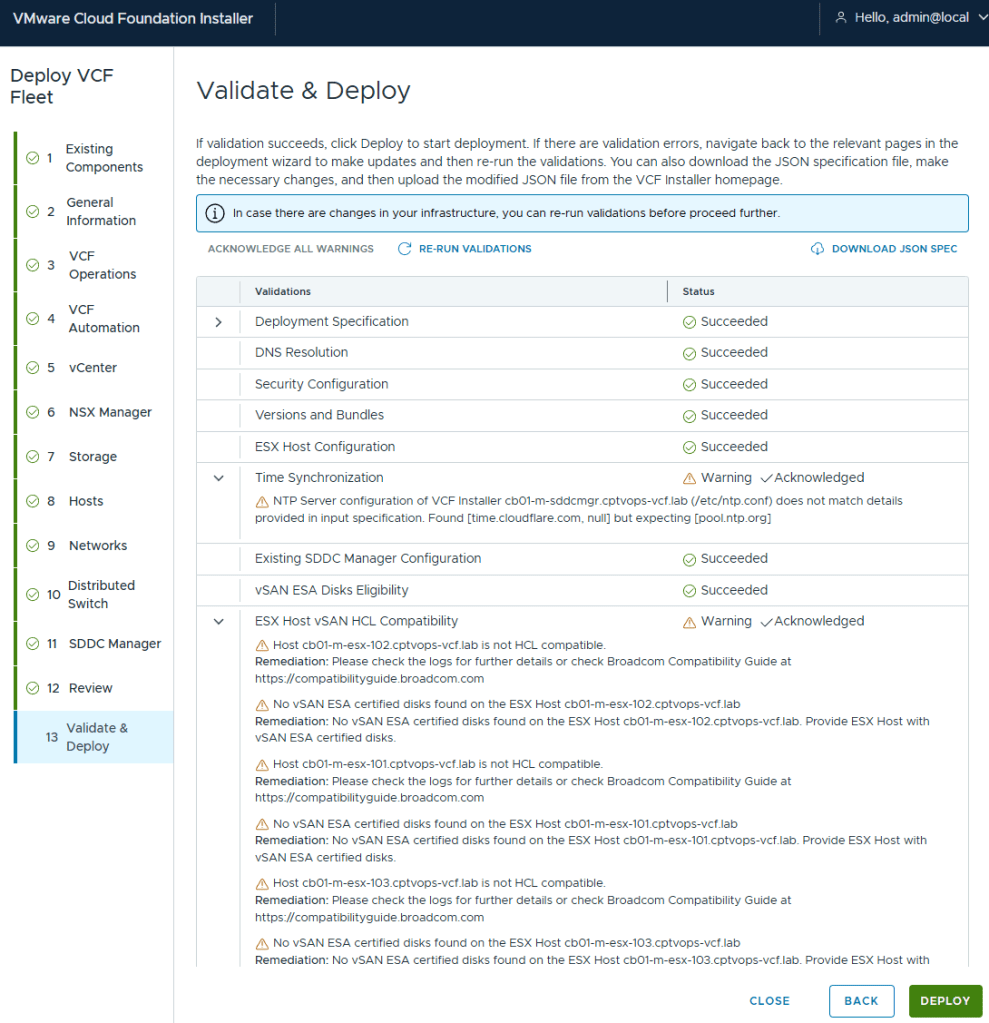
I kicked off the VCF 9 deployment in my home lab at roughly 5:03pm. The deployment finished about 7 hours later (12:23AM to be exact). Honestly, it was the NSX OVA deployment that took roughly 6 hours to complete. The VCF Fleet Manager, VCF Operations, and VCF Ops collector deployed around an hour I believe.
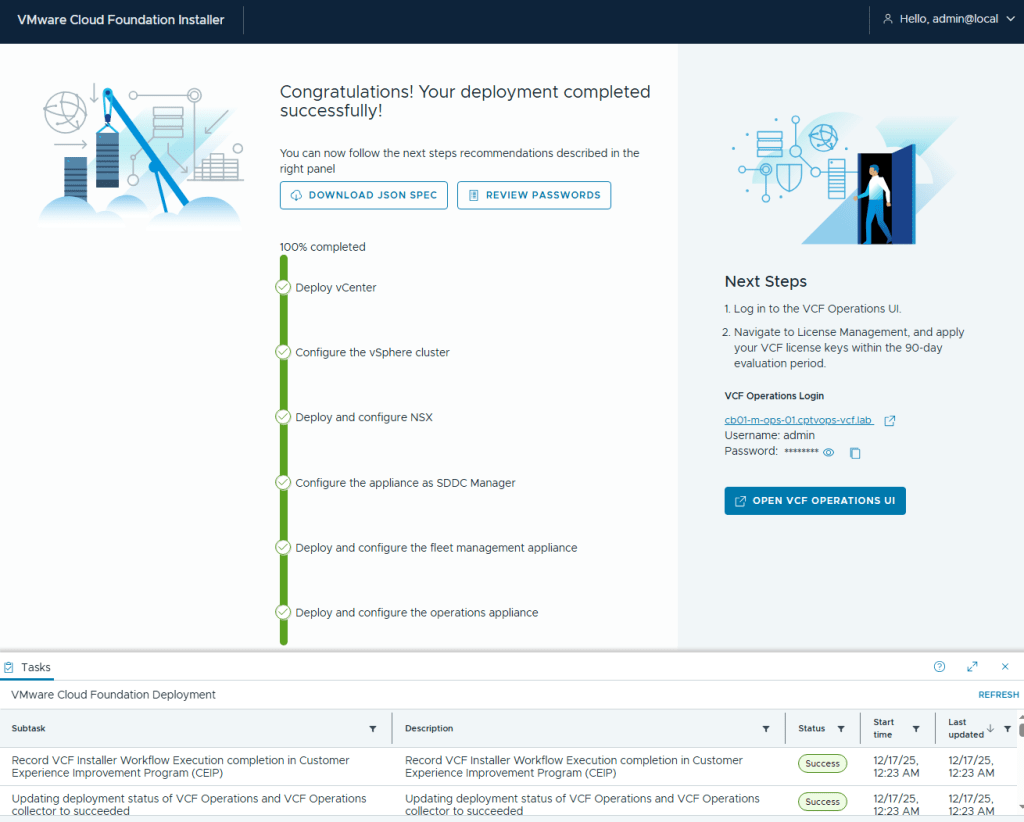
In my next blog, I’ll run through getting VCF Operations connected to the Broadcom Cloud Services portal to activate my licenses in my home lab.

Blog Date: December 2025
One of the things that I had been waiting for were the VMware Cloud Foundation 9 subscription licenses for VMUG Advantage members and the vExpert community of bloggers and SMEs. VMUG Advantage Home Lab License Guide During the week of November 17th, it was announced that the download tokens are now available for the VMUG Advantage Members who passed their VCF 9 certifications.
This post assumes that you have already deployed the VCF Installer, and are ready to get those VCF 9 bits downloaded to your home lab like a typical production environment would.
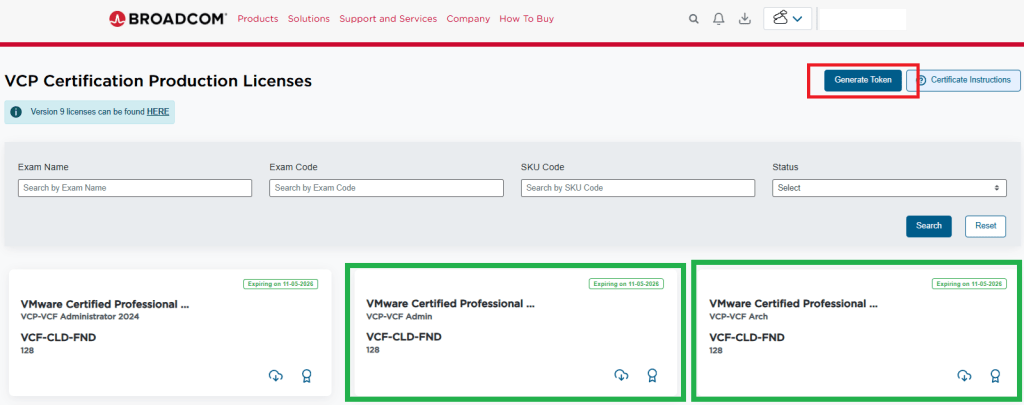
I have already requested my licences for VCF, and thus have a badge and a cloud download button on the green highlighted boxes. If you do not see those, then you would see a blue request license button. This post assumes you already have done this.
5. In the top right of the window, you see a blue “Generate Token” button. Click it.
6. On the next screen, you should see the download token needed for the VCF Installer. Copy it.
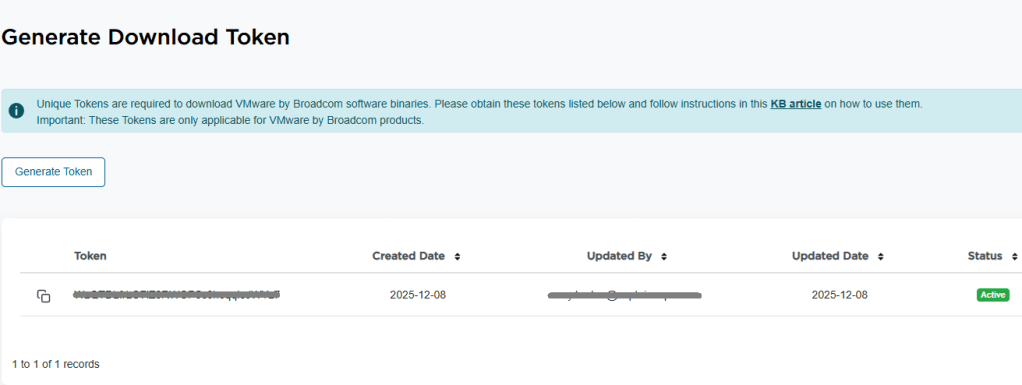
7. Log into the VCF installer appliance.
8. Go into Depot Settings, and click ‘Configure’ on the Connect to the online depot.
9. Paste the download token and click the blue ‘Authenticate’ button.
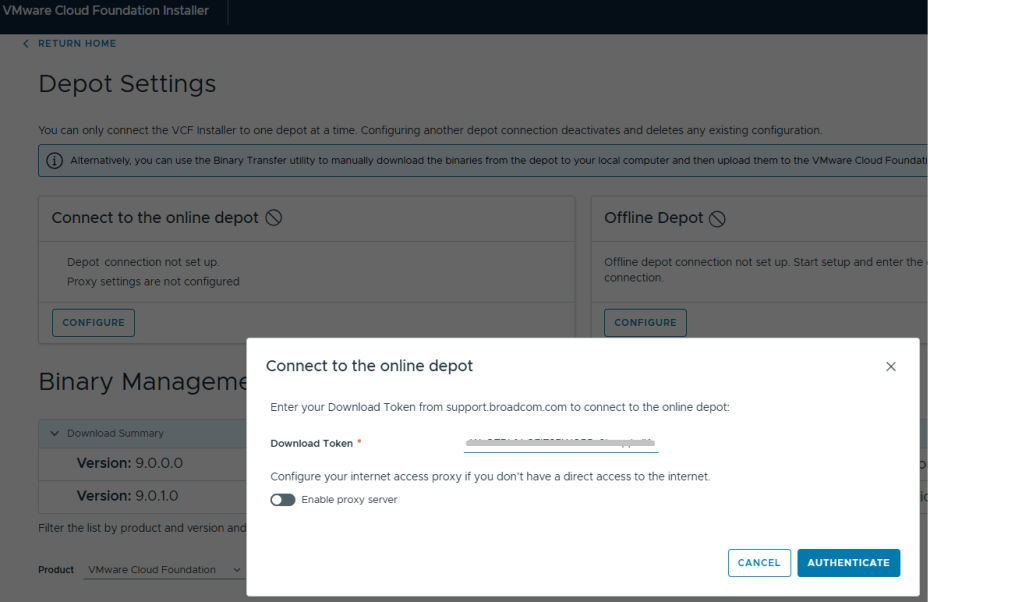
10. Assuming your VCF Installer can reach the internet and depot, a connection will be established.
11. In this example, I want to download the Product “VMware Cloud Foundation” and Version “9.0.1.0”.
12. Select all the bits desired for download, and then click the ‘DOWNLOAD’ link.
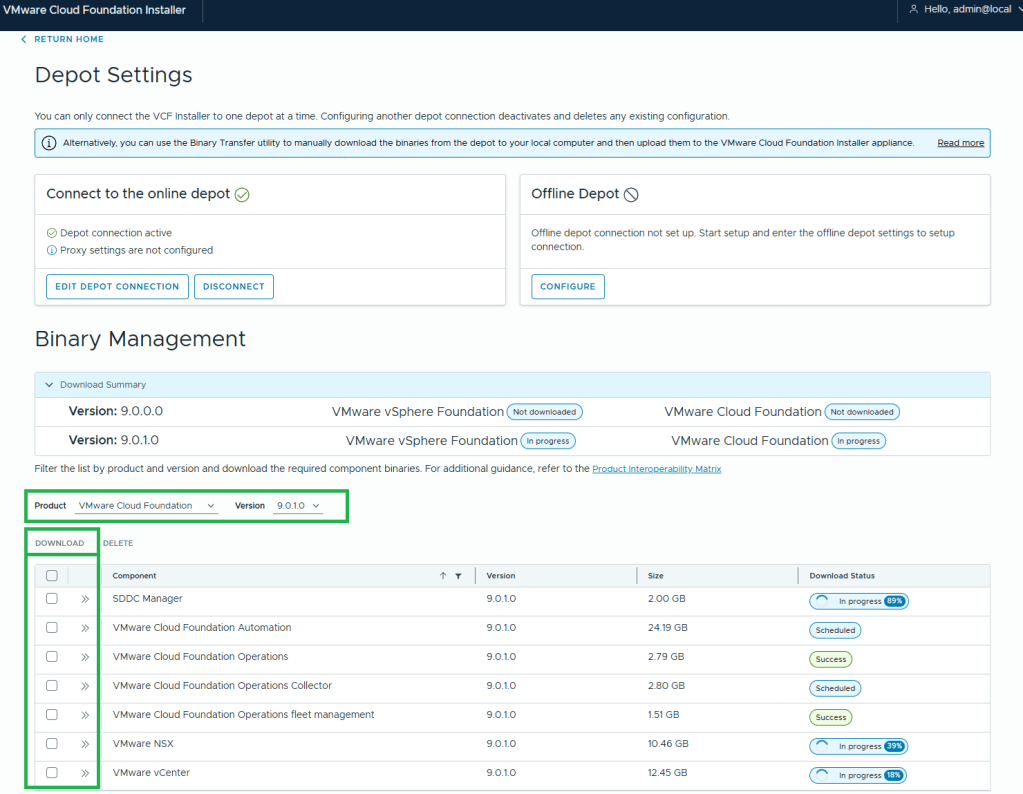
VMware by Broadcom has made this process more difficult. All of the required bits for installation used to be included with the Cloud Builder appliance that was available for VCF 5 and older versions. Now there’s an extra step to download the bits, but I’m sure that was a feature of the required download token. More complexity.

Blog Date: December 2025
In this post I’ll cover the basic ESX host prep needed for VMware Cloud Foundation. This post assumes that ESX 9 has already been installed. This post also assumes these are brand new hosts that have not been used for vsan before.
Configure the ESX Host basic network settings via the DCUI
Configure the Virtual Machine port group on the standard switch
Configure NTP on the Host(s)
Regenerate Self-Signed Certificate on ESX Hosts.
/sbin/generate-certificatesI don’t know why, but every customer engagement that I have been on, these steps get overlooked. This is probably the simplest part to preparing your data center for VCF. VMware by Broadcom also has documentation with these exact steps located here: Preparing ESX Hosts for VMware Cloud Foundation or vSphere Foundation

Blog Date: December 2025
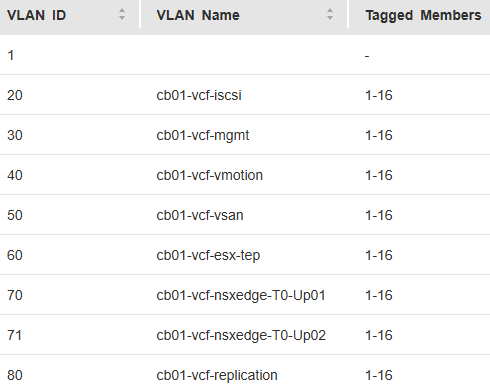
Below is the basic network Topology and vlan config for my new VMware Cloud Foundation home lab. For my home network, I had replaced my off the shelf consumer wifi router a few years ago, and purchased a Ubiquity EdgeRouter 12 so that I could have vlans for my VMware Home lab, that lasted me from vSphere 6 to vSphere 8.

On this router, I have defined and hung the vlans off from the built in virtual switch (192.168.X.1).
| vlan (10.0.X.1) | Description |
| 20 | iscsi storage straffic |
| 30 | Management |
| 40 | vmotion |
| 50 | vsan |
| 60 | ESX TEP |
| 70 | NSX Edge T0 Uplink01 |
| 71 | NSX Edge T0 Uplink02 |
| 80 | Replication |
As detailed in my VCF 9 Home lab BOM, I chose to go with the QNAP (QSW-M3216R-8S8T-US) Layer 2 for my TOR switch. This Layer 2 managed switch supports 10G on the standard ethernet ports and on the SFP+ ports, giving me lots of options for connectivity.

I can also mount two of them side by side in a standard 19 inch width rack offering more space save opportunities for future home lab expansion.

I have the same vlans tagged to the TOR switch

Blog Date: December 2025
Continuing this blog series about my new home lab, I thought I would go over the BIOS setting I have selected for these MINISFORUM MS-A2’s.
Security
— Secure Boot – Disabled
Trusted Computing
— See Device Support – Disabled
Advanced
— Onboard Device Settings
— PCI SR-IOV – Enabled
— AMD PBS (**THIS IS OPTIONAL BASED ON YOUR CONFIG**)
— PCIe/GFX Lane Configuration – x8
— GFX Lane Speed – Gen 4
— SSD0 – Gen 4
— SSD1 – Gen 4
— SSD2 – Gen 4
— AMD CBS
— NBIO Common Options
— IOMMU – Enabled
— PSPP – Performance
— FCH Common Options
— AC Power Loss – Previous
— SMU Common Options
— TjMax – 78
In my next Blog, I will cover my basic network set.
You must be logged in to post a comment.